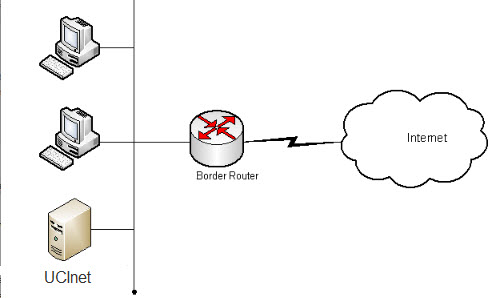
OIT used the holiday break as an opportunity to upgrade the border router and campus firewall, improving network performance and reliability. The timing was chosen to minimize the impact on the campus community who rely on UCInet Internet connectivity.
Prior to this project, UCI had a single system providing the link between UCInet and the Internet, and this device was also responsible for providing the campus firewall service. This represented a vulnerability, in that hardware failure could result in loss of connectivity.
The border router was also aging, having been put into service in August of 2003, and Cisco had announced the end of maintenance for this model later this year.
The project replaced the components within the border router, added a second border router, distributed Internet services between them, and isolated the firewall service to its own redundant systems. Tests have demonstrated a significant increase in network bandwidth as well. Now if one of the two routers should go down, connectivity will be sustained by the redundant architecture of the new system.
The current arrangement also makes use of Cisco’s Virtual Switching System technology, allowing the two routers to be managed as a single service.
An upcoming goal is to house the two border routers in different buildings. One will remain in Central Plant, and the other will be housed in OIT’s SSPA network vault. This geographic distribution will further reduce the risk that loss of power or other facilities to a single building could interrupt UCI’s connection to the Internet.